Defence
Installing Cloud Custodian
python3 -m virtualenv custodian
source custodian/bin/activate
pip install c7n
Writing policy
A policy specifies the following items
- The type of resource to run the policy against
- Filters to narrow down the set of resources
- Actions to take on the filtered set of resources
Policy to look for public access buckets
- Create new policy
vi s3-public-access.yml
policies:
- name: s3-global-access
description: |
Finds global access s3 buckets in your account
resource: s3
region: ap-south-1
filters:
- type: global-grants
actions:
- no-op
- We can validate the policy before executing by running the following command
custodian validate s3-public-access.yml
- Perform the dryrun by running the following command
custodian run --dryrun -s output s3-public-access.yml
- Execute the policy by running the following command
custodian run -s output s3-public-access.yml
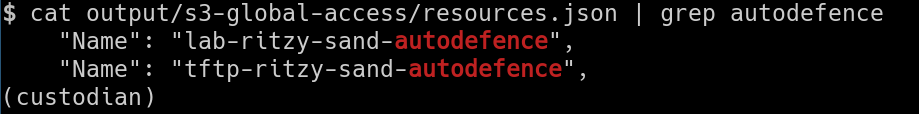
- Then access the buckets public using
cat output/s3-global-access/resources.json | grep autodefence
Applying the changes to fix this issue
- Update the policy with below changes
vi s3-public-access.yml
policies:
- name: s3-global-access
description: |
Finds global access s3 buckets in your account and fix them
resource: s3
region: ap-south-1
filters:
- type: global-grants
actions:
- type: delete-global-grants
grantees:
- "http://acs.amazonaws.com/groups/global/AllUsers"
- "http://acs.amazonaws.com/groups/global/AuthenticatedUsers"
- Now validate and execute the policy to apply the changes to fix the s3 buckets public access
custodian validate s3-public-access.yml
custodian run --dryrun -s output s3-public-access.yml
custodian run -s output s3-public-access.yml
- Then run the
slurpto scan for the s3 buckets again to see if the defence applied
./slurp internal
The result will not return any Public S3 buckets that we created