Logging
Ensure CloudTrail is enabled in all regions
- Navigate to CloudTrail console
- Click on Create Trail
- Enter a
Trail nameand chooseYesforApply trail to all regions
- Under
Storage location, chooseYesto Create a new S3 bucket and give a unique name forS3 bucket - Click on
Advancedand chooseYestoEncrypt log files with KMSandCreate a new KMS key. Give a KMS key name - Choose
YesforEnable log file validation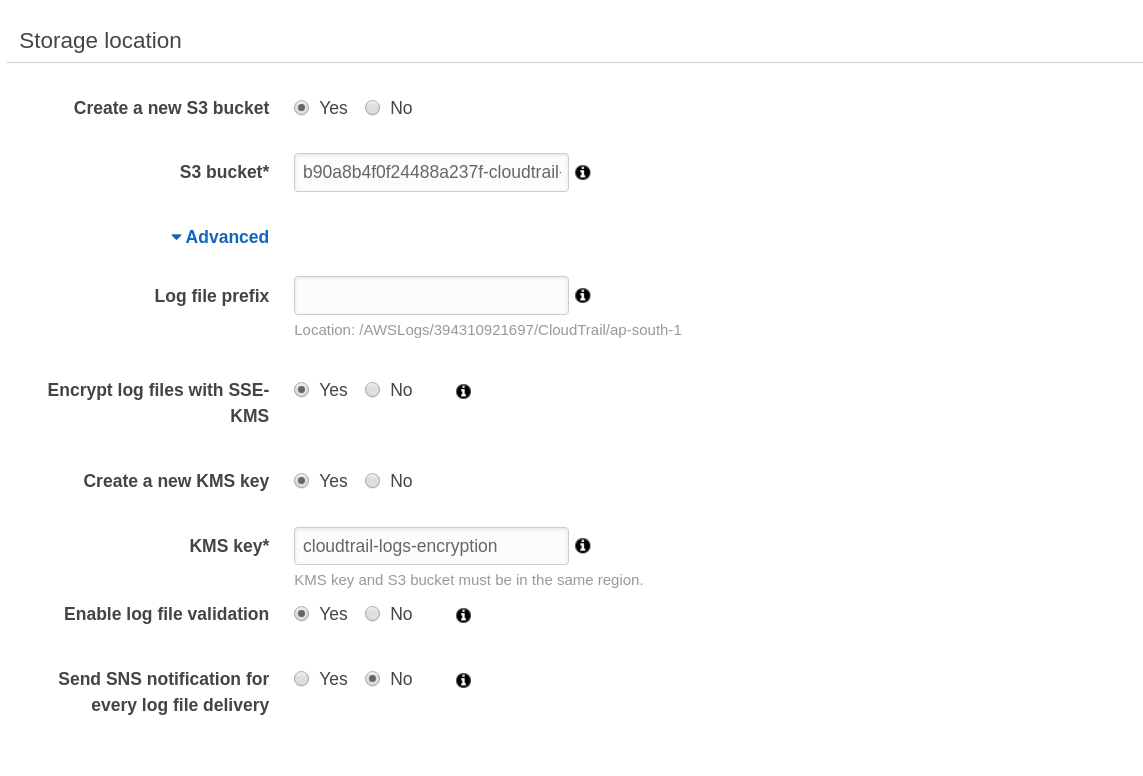
Ensure CloudTrail trails are integrated with CloudWatch Logs
- In the CloudTrail console, click on
Trailson the left panel - Click on the Trail created in previous step
- Scroll down to find
CloudWatch Logsand click onConfigure - Leave the default CloudTrail log group name and click on
Continue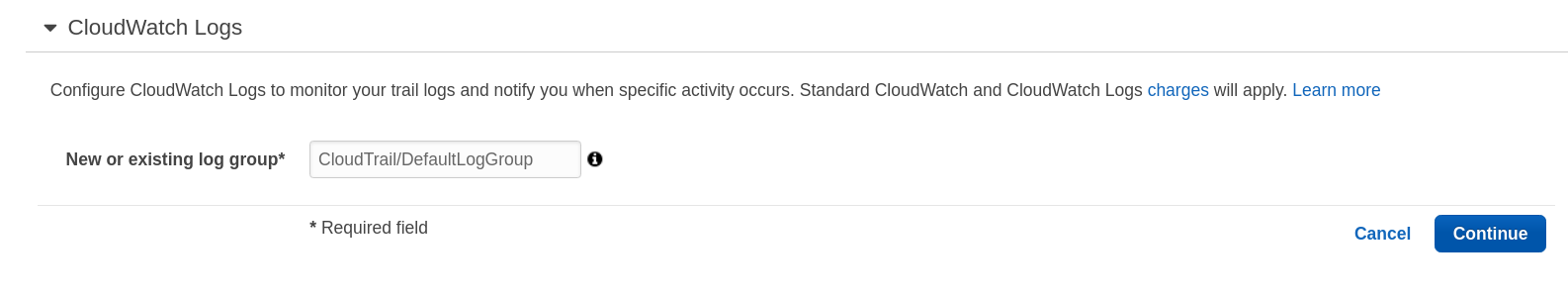
- You will be prompted to create a Role with which CloudTrail with put logs to CloudWatch. Click on
Allowat the bottom,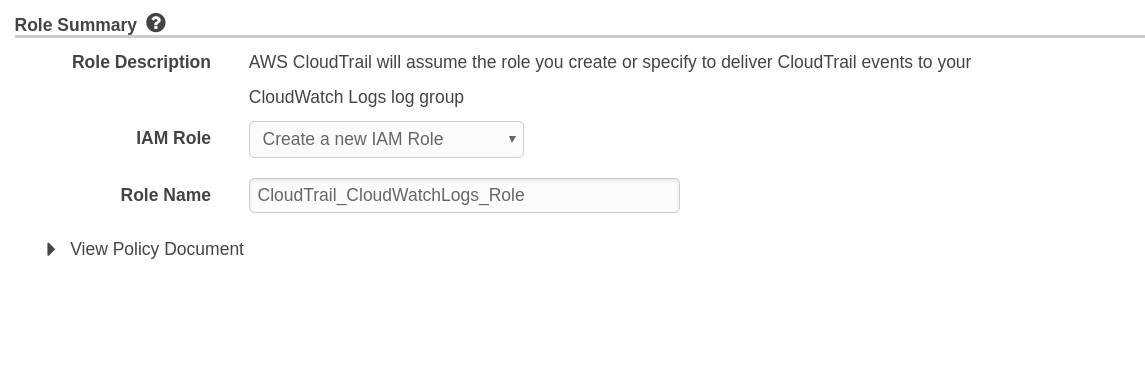
Ensure S3 bucket access logging is enabled on the CloudTrail S3 bucket
- Navigate to S3 console
- Click on the CloudTrail bucket created previously
- Click on
Propertiestab - Click on
Server Access Logging - Select
Enabled - Choose the bucket created during CloudTrail creation part as Target and enter a
Target Prefix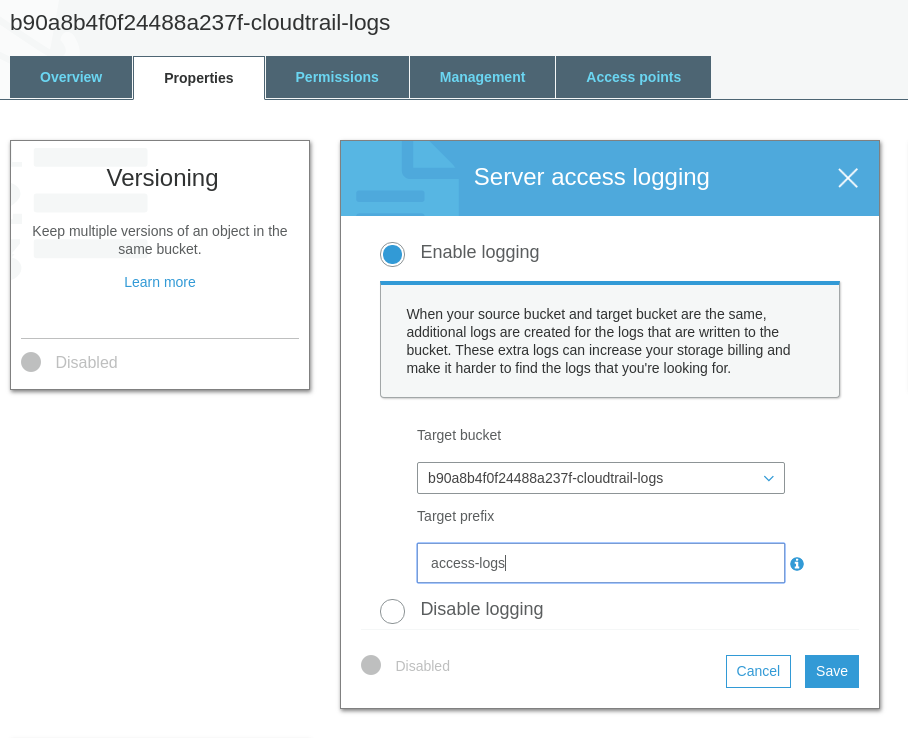
Ensure VPC flow logging is enabled in all VPCs
Get VPC ID
Note down the VpcId
aws ec2 describe-vpcs
Create Log Group
aws logs create-log-group \
--log-group-name vpc-flow-logs
Create IAM Role
Policy to write to CloudWatch
Save to a file /tmp/vpc_cloudwatch_role.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "vpc-flow-logs.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
Create role with Trust Policy document
aws iam create-role \
--role-name flowLogsRole \
--assume-role-policy-document file:///tmp/vpc_cloudwatch_role.json
Attach Role policy to role created
aws iam attach-role-policy \
--policy-arn 'arn:aws:iam::aws:policy/CloudWatchLogsFullAccess' \
--role-name flowLogsRole
Enable Flow logs
aws ec2 create-flow-logs \
--resource-type VPC \
--resource-ids <VPC_ID> \
--traffic-type REJECT \
--log-group-name vpc-flow-logs \
--deliver-logs-permission-arn <IAM_ROLE_ARN>
<VPC_ID> and <IAM_ROLE_ARN> should be substituted before running the previous command. The create command should be repeated for all VPCs